







The “exploit” is trivial and embarrassingly easy.����
These are words you never want to hear when talking about vulnerabilities in a widely used product, but that’s exactly how John Hammond, Principal Security Researcher at �Ӱɴ�ý, described the ability to exploit the ConnectWise ScreenConnect vulnerabilities in the �Ӱɴ�ý Team’s technical analysis. Then you see a headline in that reads, “‘I can’t sugarcoat it — this shit is bad,' said �Ӱɴ�ý' CEO,” and you know this is not your everyday cybersecurity event.
ConnectWise ScreenConnect is a popular software used to monitor and manage systems remotely. On February 19th, ConnectWise issued an advisory that all versions below 23.9.8 of their on-prem version of ScreenConnect had two vulnerabilities (CVE-2024-1709 and CVE-2024-1708) and urged their users to patch immediately. Normally, this would not be a cause for alarm. However, one of the vulnerabilities was given a CVSS score of 10 out of 10, meaning it was the highest level of severity. As in, “stop whatever you’re doing and patch now” level of seriousness.
What drove this urgency? Well, at first, we weren’t really sure. There were precious few details provided with the announcement. So, the �Ӱɴ�ý research team immediately jumped into action, trying to learn as much as possible.��It took less than two hours before they were able to understand the exploit and build a proof of concept (PoC) exploit. While some of this was no doubt due to the amazingly smart humans at �Ӱɴ�ý, it was also a testament to how basic this vulnerability was and how easy it would be for an attacker to exploit.��
You can read exactly how we conducted our research and built the PoC, as well as all the technical details about what we found, in our blog. If you’re like me and just want the easy version, here is how simple the SlashAndGrab vulnerability is to exploit.
Step 1: Go to setupwizard.aspx. This is where you set up ScreenConnect the first time. If ScreenConnect was already set up, there would be nothing to see or do here.
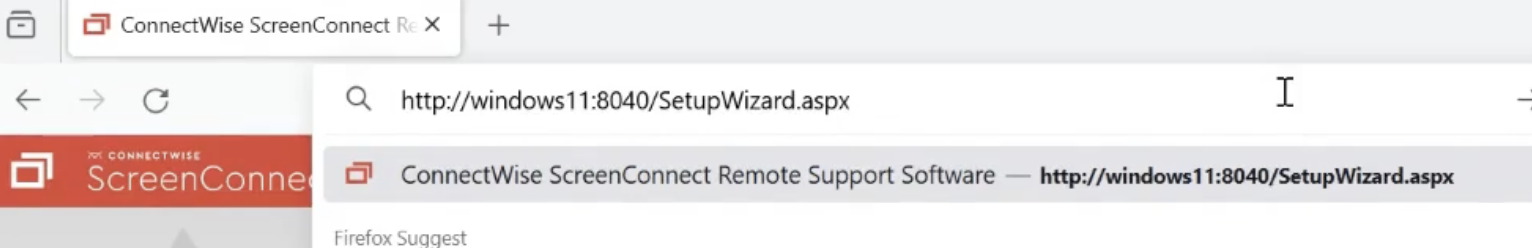
��Step 2: Add a forward slash “/” to the end of the address.
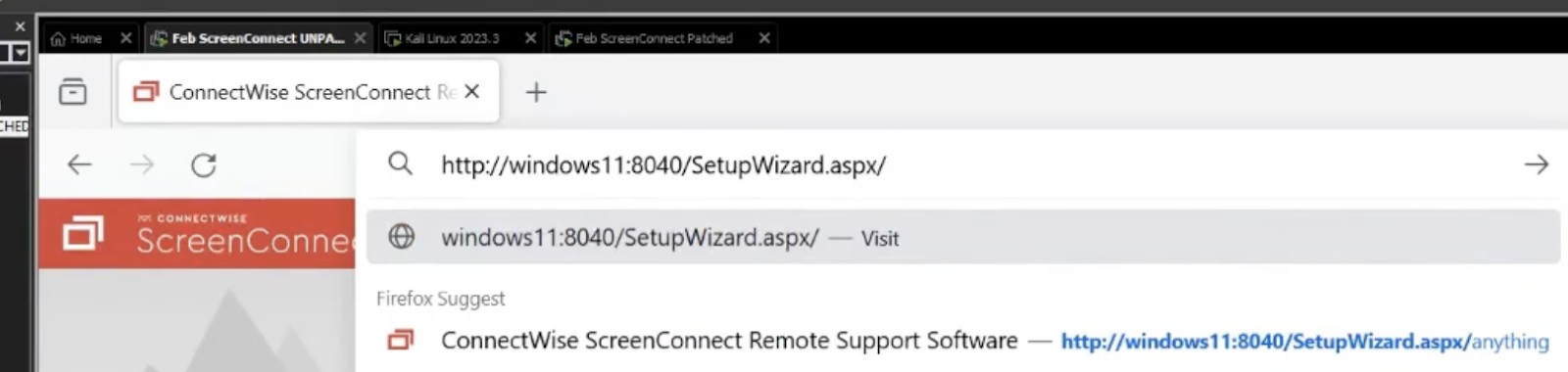
Step 3:�� You are in. This takes you to the “Welcome To ScreenConnect” setup. You can now create your own username and password and gain full access.
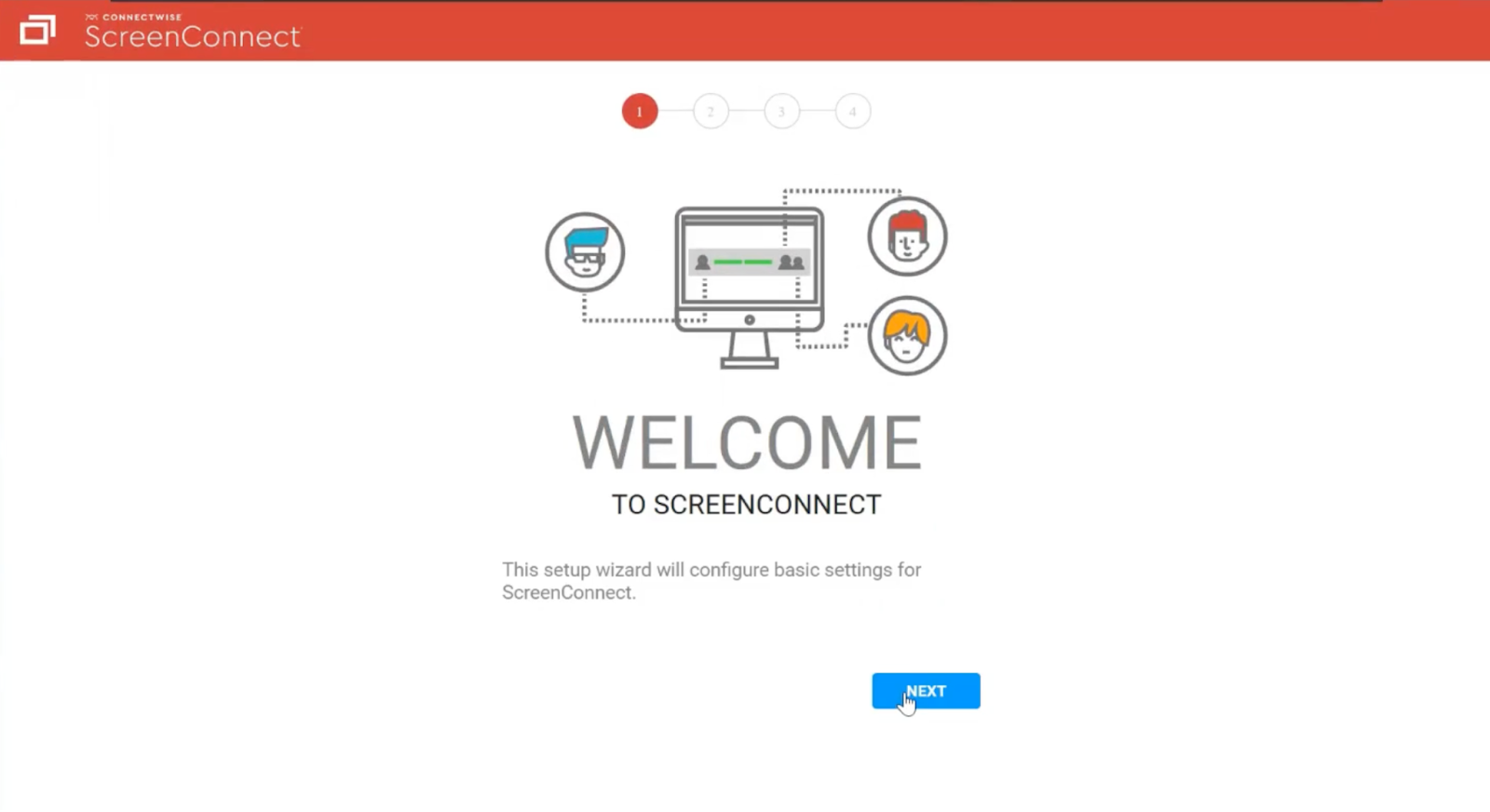
That’s it. That’s the hack. And now you know why we call it SlashAndGrab.
When one of my teammates first realized what it took to exploit, he said, “It's so simple my 13-year-old could do it.”��He wasn’t exaggerating.��However, as you can see from our research articles, that doesn’t prohibit the technical analysis from getting pretty deep in the weeds (especially for a layperson).��Some technical terms you’ll hear relating to this hack include “Authentication Bypass” and “Path Traversal.” An Authentication Bypass is a flaw that allows attackers to go around security checks and access restricted areas without the proper permissions. Path Traversal enables attackers to access files or directories on the server that they shouldn't be able to reach.
There were thousands of vulnerable ScreenConnect servers. Unfortunately, many who were unable to patch in time suffered serious consequences.��Within 48 hours of the exploit PoC becoming public, �Ӱɴ�ý reported that, “the adversaries taking advantage of this vulnerability have been VERY busy.” Attackers were using their new access to do all sorts of devious things, including dropping ransomware, cryptocurrency coin miners, and additional remote access to retain a presence on devices even after the ScreenConnect vulnerabilities were resolved.

We found out about the vulnerability (with scarce details) on Monday afternoon.��Our research team immediately started digging into the patch to understand better what it was intended to do.��In only a few hours, �Ӱɴ�ý had successfully built a PoC.��The PoC confirmed what ConnectWise was indicating, that, as our CEO Kyle Hanslovan said in a headline, “this shit is bad.”����
Once we understood the details and gravity of the situation, we immediately sounded the alarm to every �Ӱɴ�ý partner who had a vulnerable version of ScreenConnect.��In total, we sent over 1,600 incident reports with clear directions on what they needed to do.��We also published a blog encouraging anyone in the community to patch immediately.��This was not a drill.����
It’s important to note that while we had a working PoC and now understood the details of the vulnerability, we did not divulge any information that could tip off hackers.��Doing so would have been like handing over an instruction manual to the bad guys, especially given the simplicity of the exploit.����
At this point, we knew IT and security folks across the industry were getting nervous.��While we were still echoing the message that they needed to patch immediately, we also published a second blog with detailed detecting guidance so they could start looking into any potentially related malicious activity. This quickly became the go-to resource for anyone looking to conduct defense-in-depth detections.���Ӱɴ�ý then , which would help speed up the hunt for many in the community.��
Rather than just sitting on our hands and waiting for things to get bad (really, really bad), we did something proactive.��We released a “mitigation” vaccine to hosts running the vulnerable version.��This hotfix would keep our partners safe until they were able to patch. Unlike many others, �Ӱɴ�ý EDR is built on our own tech. This gives us the ability to react faster and more nimbly than those relying on third parties, and the SlashAndGrab vaccine is a perfect example of that.��
The vaccine we released to impacted endpoints was deployed before any public details about the vulnerability were released and before we had heard of in-the-wild exploitation.��Fortunately, it worked, and very few of our partners were impacted.��Once again, we heard lots of comments from our partners that, “�Ӱɴ�ý, saved my ass!”����
Once the PoC and other exploit details were unfortunately shared by multiple parties and were widely available to the public, we released our full detailed analysis of SlashAndGrab. This would help the community better understand the severity of the event, emphasizing the need to patch immediately and continue to provide detection guidance to ensure they had not been compromised.��Again, this information was withheld until it was ethical to share.��
While the �Ӱɴ�ý Security Operations Center (SOC) was detecting and kicking out active adversaries, we were able to start tracking what the hackers were doing with the access they were able to gain from the SlashAndGrab ScreenConnect exploitation.��
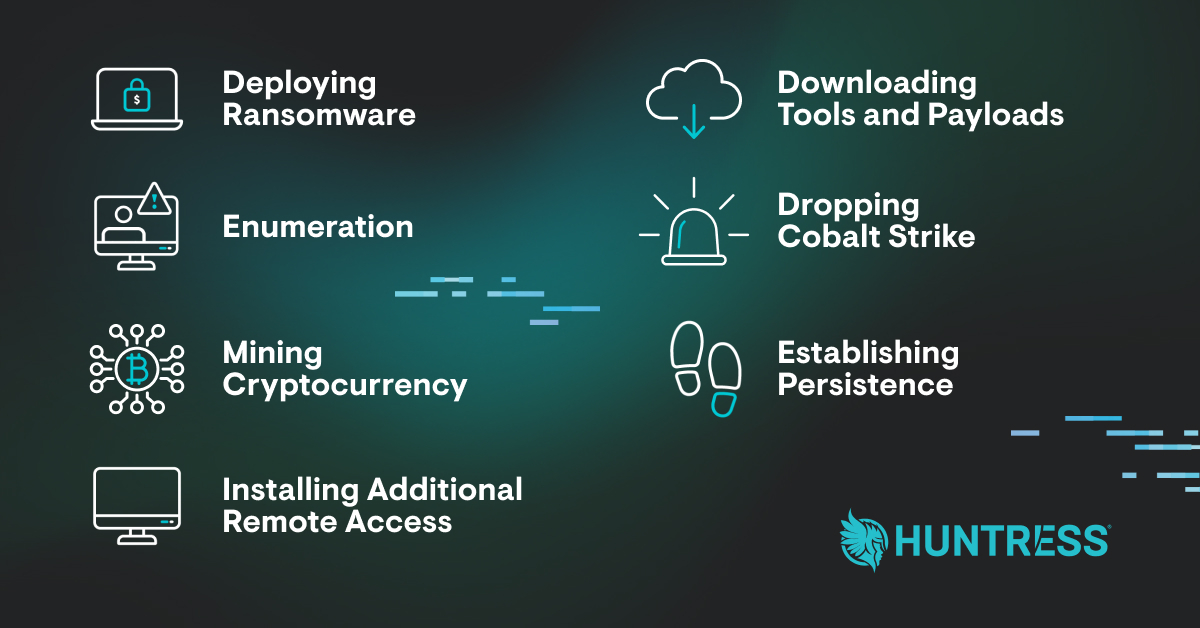
�Ӱɴ�ý once again led the way for community research by publishing a detailed report about post-exploitation tradecraft. This helped the community know what activity to look for so they could better hunt for adversaries and keep their organizations safe.������
Note: If you’re wondering how �Ӱɴ�ý had partners impacted if we issued a hotfix, it's because not every partner deploys �Ӱɴ�ý to all their customers or all their endpoints.��So, unfortunately, some were left unprotected.��Additionally, we took on many new customers and partners who took advantage of our free trial to get outside help after they realized they may have been hacked.����
Get insider access to �Ӱɴ�ý tradecraft, killer events, and the freshest blog updates.
