






Periodically, a large scale cybersecurity issue requires āall hands on deckā from the ŠÓ°É“«Ć½ Team (seeĀ ,Ģż,Ģż). The unfoldingĀ Ā fiasco also happens to be one of those moments. Weāve created this blog is to provide simple answers to a complex supply chain attack affecting global IT Departments.
The hardware manufacturer ASUS included an application on all of their Windows devices called Live Update.Ā , Hackers compromised ASUSā automatic updating infrastructure and pushed backdoored updates via the Live Update software. Kaspersky Lab suggests that over a million hosts may have run a backdoored update.
The purpose of the backdoored update was to validate whether the affected computer was a target of interest. If the computer was of interest,Ģż. If it was not of interest, no additional payloads were installed. Itās estimated approximately 600 computers were targeted.Ā Considering this very selective attack, your ASUS computers likely were not infected.Ā On March 26th,ĢżĀ that all ASUS computers/laptops running Live Update should be updated to version 3.6.8 āto resolve security concernsā.
To give our partnerās peace of mind, the ŠÓ°É“«Ć½ Development Team created custom tools to discover any computer, laptop, or server running Live Update below version 3.6.8 (huge thanks toĀ Ā for being our guinea pig!)
The ThreatOps Team has reported all hosts running an outdated Live Update application and weāll continue to monitor the situation for any updates or new agents that come online.
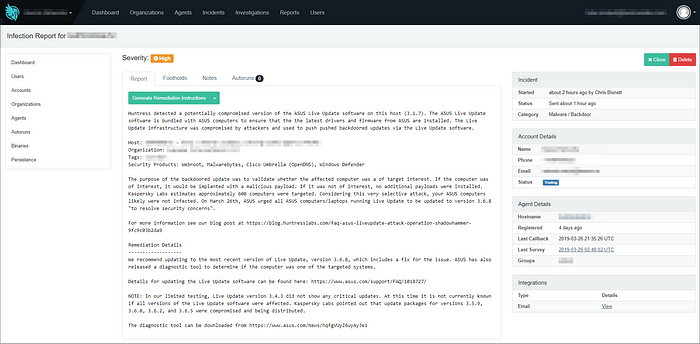
All backdoored updates for Live Update included a modified version of Setup.exe. Within this application, the attackers added an obfuscated shellcode payload (this is what was looking for the targeted MAC addresses).
If your computer was not targeted, the shellcode will create a file called idx.ini similar to the following example:
As a result of this discovery, you can search your file system for the idx.ini file to determine if a backdoored update was run on your host!
ās blog dives into the technical implementation of this much deeper andĀ Ā to a directory up to two levels higher than where Setup.exe was executed.
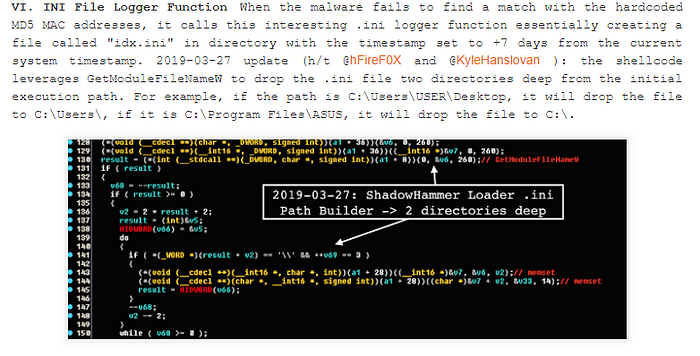
Only 600 hosts were targeted with the second stage malware which means you and your clientsĀ likelyĀ didnāt receive the attention of a nation-state adversary šµļø ā(sorry to disappoint). However, we totally understand the difference between assuming and knowing you werenāt targeted.
For those looking to verify if their computer was on the hit list, check out the security diagnostic tools release byĀ Ģż²¹²Ō»åĢż. These applications will gather host details like the MAC address and cross reference your data against list of targeted MAC addresses.
Hesitant to run the software?Ā Ā and releasedĀ Ā that were targeted which you can check against. AĀ Ā which allows you to manually submit your ASUS computerās MAC address.
If a diagnostic tool indicated youāre targeted, weāre here to help! Contact us at support[at]huntress.io and weāll have someone quickly reach out to you.
With that said, it should be noted that one of the targeted MAC addresses belonged to a generic VMware interface:
In this case, the backdoored update actually checked for the presence of two MAC addresses. As long as your other NIC did not have MAC address 70:77:81:C0:FD:49, youāre likely in the clear.
According toĀ Ā on March 26th, 2019, Live Update version 3.6.8 was released. ASUS specifically highlighted this new version:
ā¦introduced multiple security verification mechanisms to prevent any malicious manipulation in the form of software updates or other means, and implemented an enhanced end-to-end encryption mechanism.
The US Cybersecurity and Infrastructure Security Agency (CISA)Ā Ā about Live Update version 3.6.8 stating:
This version addresses vulnerabilities that a remote attacker could exploit to take control of an affected system. These vulnerabilities were detected in exploits in the wild.
For IT Departments or Managed Service Providers looking to upgrade Live Update to version 3.6.8, please followĀ .
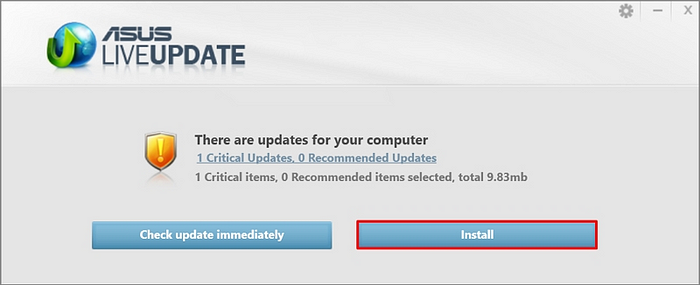
While working with our partners, we observed some issues with Live Update checking for updates:
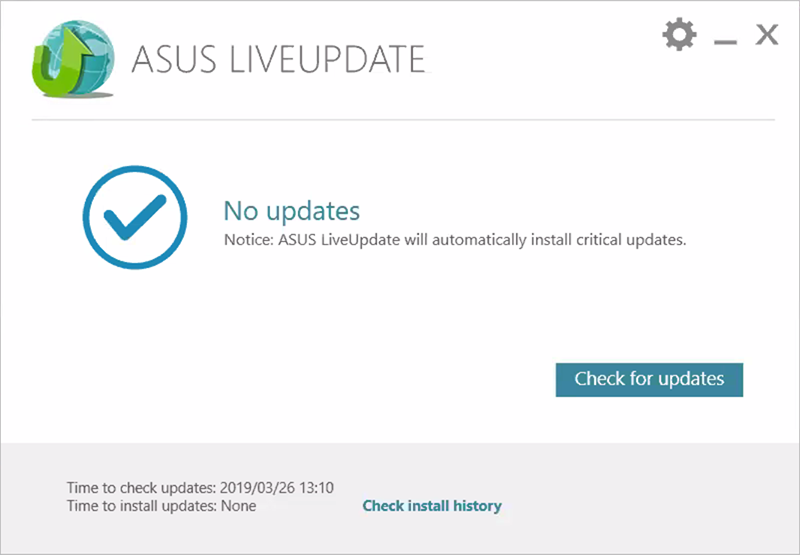
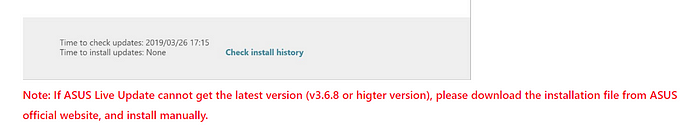
As demonstrated above, at least some hosts running Live Update below version 3.6.8 are not receiving the new update. ASUS noted this could happen in their support documentation. Unfortunately, we have not found a manual installer for version 3.6.8.
Itās very likely this issue will garner media attention as details continue to unfold. IT departments and Managed Service Providers should leverage this opportunity to demonstrate their ability to address breaking cybersecurity incidents.
Weāre currently creating some resources to help you articulate what was done to ensure your companyās and clientās security. Stay tuned!
This situation is still unfolding. Check the section frequently for updates!
On March 25th, 2019, journalistĀ Ā dropped anĀ Ā detailing the supply chain attack against ASUSā Live Update. Shortly after,ĢżĀ with a handful of indicators of compromise (IOC) which included four malicious .ZIP files:
These .ZIP archives contained a setup .EXE and two .MSI files. The MSI files also extracted over a dozen applications and configuration files for Live Update. This made determining the backdoor less trivial.

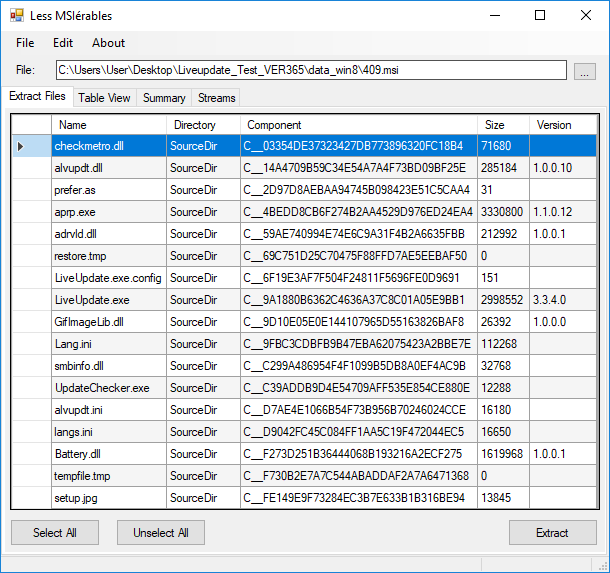
Researchers on Twitter also pointed out that Setup.exe was specifically backdoored to decrypt and run the attackers payload.
Using these details, the ŠÓ°É“«Ć½ ThreatOps team gathered known malware samples and started the analysis process to understand which parts of Live Update was actually compromised.
Get insider access to ŠÓ°É“«Ć½ tradecraft, killer events, and the freshest blog updates.
