






UPDATE:Ь§Read our full analysis of CVE-2024-1709 & CVE-2024-1708 and detection guidance here.
On February 19, 2024, ConnectWise released an related to the disclosure of two vulnerabilities affecting their ScreenConnect software. This advisory was tagged by ConnectWise with a severity of тCriticalт and a priority of т1 - High.т
The агАЩДЋУН team was able to successfully reproduce and weaponize the vulnerability for CWE-288 Authentication bypass using an alternate path of channel. The POC for this vulnerability was recreated with ease and required minimal technical knowledge and resources. Given this, агАЩДЋУН immediately released a post on this vulnerability and its potential impact. While агАЩДЋУН strongly recommends immediately patching any ConnectWise software to version 23.9.8, the following is detection guidance for defense-in-depth.
Upon executing the POC, агАЩДЋУН examined the User.xml file located in: C:\Program Files (x86)\ScreenConnect\App_Data\. The contents of this file may contain the following:
<?xml version="1.0"?>
<Users xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<User>
Ь§<CreationDate>[IMPACT-TIMESTAMP]</CreationDate>
Ь§<Email>anyemailaddress@theinternet.com</Email>
Ь§<IsApproved>true</IsApproved>
Ь§<IsLockedOut>false</IsLockedOut>
Ь§<LastActivityDate>0001-01-01T00:00:00</LastActivityDate>
Ь§<LastLockoutDate>0001-01-01T00:00:00</LastLockoutDate>
Ь§<LastLoginDate>0001-01-01T00:00:00</LastLoginDate>
Ь§<LastPasswordChangedDate>[IMPACT-TIMESTAMP]</LastPasswordChangedDate>
Ь§<PasswordAttemptWindowStartTime>0001-01-01T00:00:00>/PasswordAttemptWindowStartTime>
Ь§<InvalidPasswordWindowAttemptCount>0</InvalidPasswordWindowAttemptCount>
Ь§<InvalidPasswordAbsoluteAttemptCount>0</InvalidPasswordAbsoluteAttemptCount>
Ь§<Name>Administrator</Name>
Ь§<PasswordHashHistory>
Ь§ <base64Binary>[REDACTED-BASE64]</base64Binary>
Ь§</PasswordHashHistory>
Ь§<Roles>
Ь§ <string>Control Administrator</string>
Ь§</Roles>
</User>
</Users>
Note that the 0001-01-01T00:00:00 timestamps indicate that there is no sane value yet. When a new user is just created, it does not yet have a LastLoginDate or LastActivityDate.
To be clear, this User.xml file will be modified any time any user performs any activity. This was verified via that this User.xml file was overwritten after each successful attempt. This makes definitive identification of exploitation difficult, but unfortunately from our investigation, we found limited options for logging and forensic artifacts on a ScreenConnect server. If the newly created user were to log in, the timestamps would, of course, be updated. If the timestamps are not nulled, then this would indicate that the user has actually logged into the instance recently.
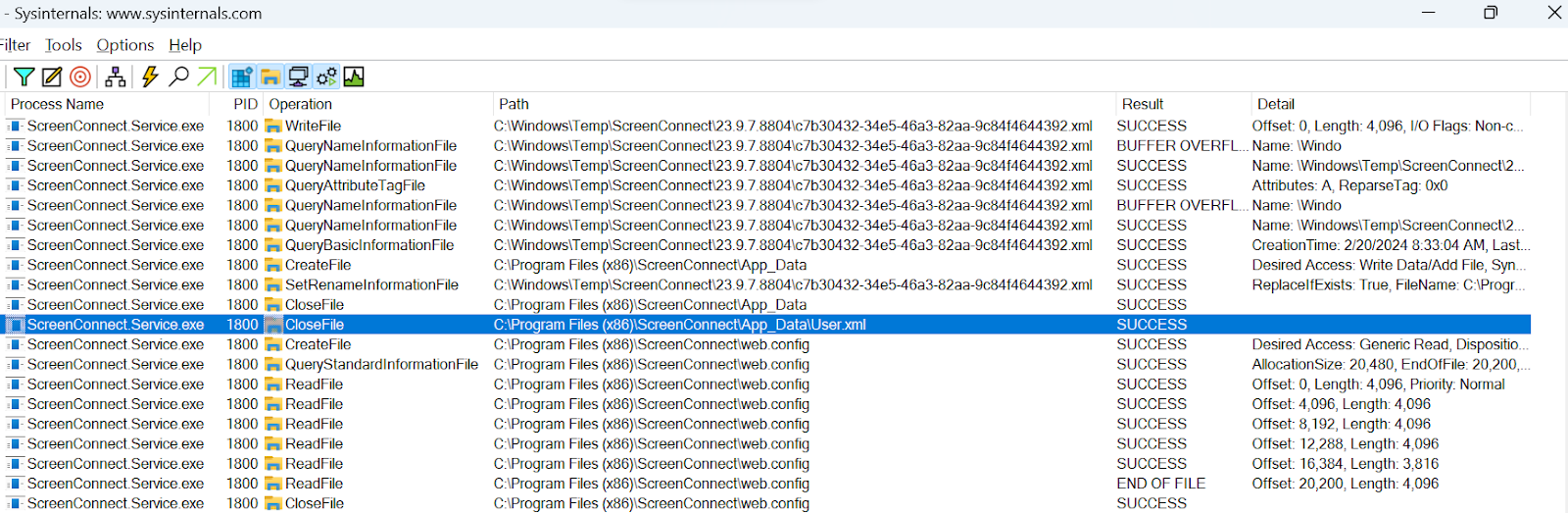
Itтs important to note that the <random_value>.xml file in C:\Windows\Temp\ScreenConnect\23.9.7.8804\ is created on disk, but immediately removed. The GUID in the file name appears to be unique for each instance. These files are recoverable via disk forensics, however, which can help you recover previous attacker activities.
By configuring a hostтs Advanced Auditing policy to log a successful event and with a SACL set on the directory, we can see when the file is being modified.
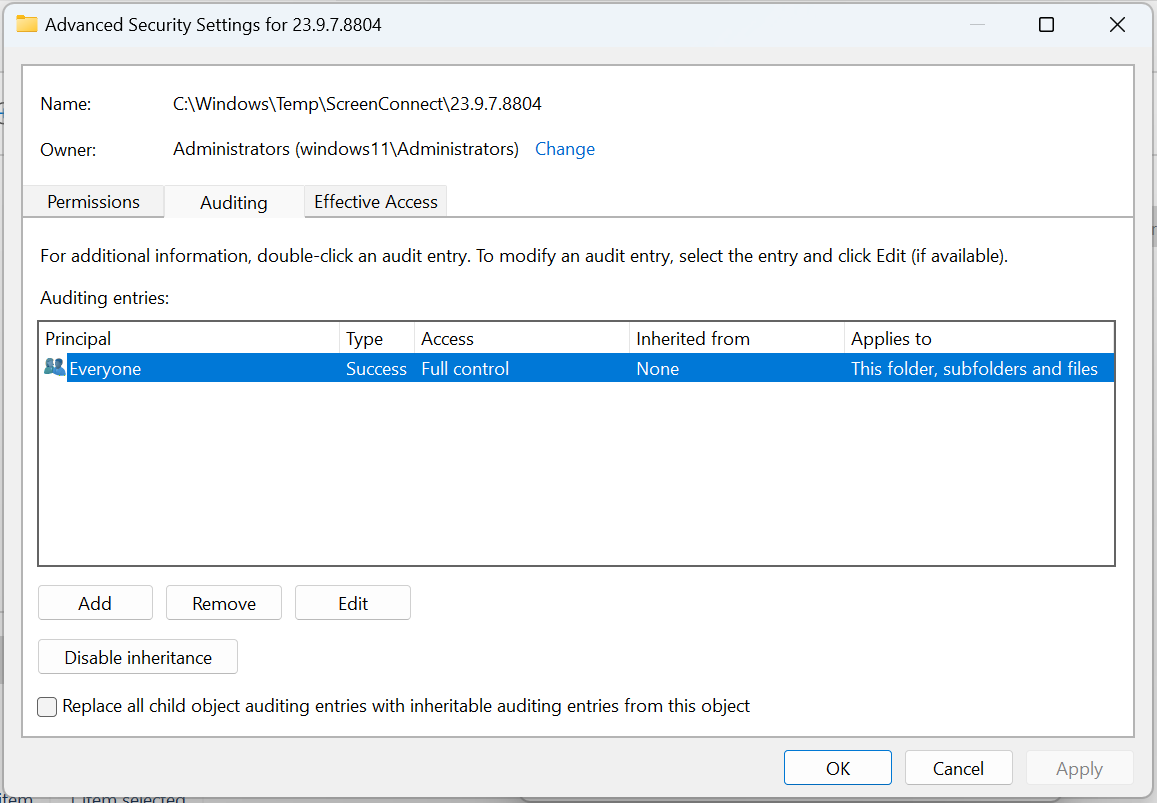
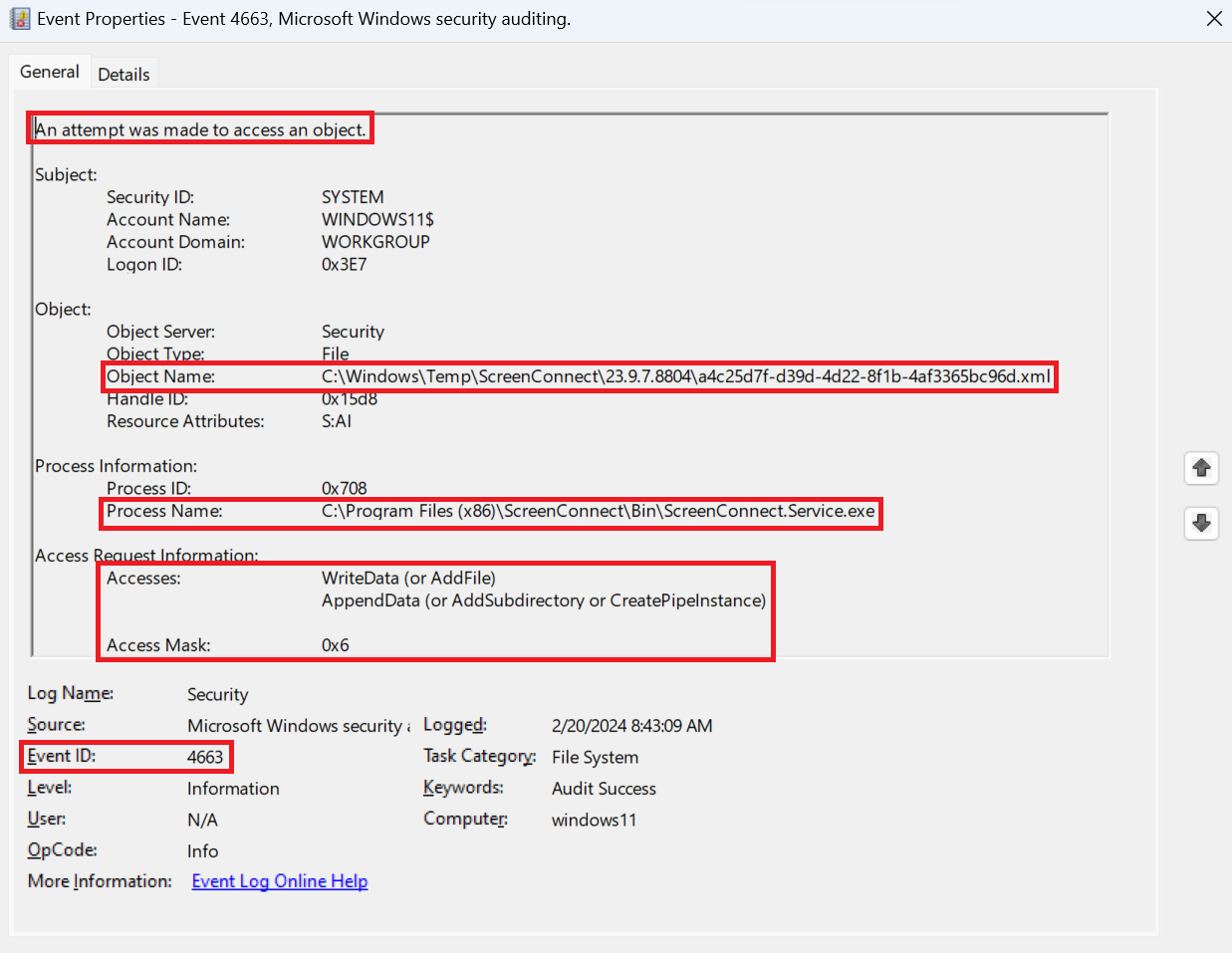
This event can be forwarded to a SIEM, and with the contents of the User.xml file itself, we have a greater level of context to examine if an attack has occurred.
The aforementioned artifacts may be reviewed for DFIR/threat hunting purposes if an attacker has leveraged this exploit against a target system to see if an account was created outside of normal operating procedures. However, the artifacts alone may not be enough for a definitive indication or provide enough context for analysis and triage to indicate that the exploit was leveraged.
In addition to the artifacts mentioned in this blog, we also observed evidence of exploit execution within the IIS logs. We will forgo demonstrating the contents of these IIS log entries for now, until weтve seen exploitation in the wild since doing so would tip our hand to the attackers.
Happy Hunting!Ь§Ь§
Stay tuned for more details as this unfolds.
Special thanks to John Hammond, Caleb Stewart, Dave Kleinatland, Andrew Schwartz, Jason Phelps, Jai Minton, Tim Kasper, Andrew Kaiser, Jason Slagle, Jamie Levy, and many others for their contributions to this write-up.
Get insider access to агАЩДЋУН tradecraft, killer events, and the freshest blog updates.
