







On Tuesday, August 29, 2023, the that they and other international partners disrupted the Qakbot malware infrastructure in a successful takedown.
First things first, this is awesome!!!
This is phenomenal news and incredible strides for our industry. This effort demonstrates international collaboration across both public and private partnerships and it makes a massive impact, not only on the Qakbot botnet strain, but also on the ransomware syndicates that make use of it.
In their announcement, the FBI stated Operation “Duck Hunt” succeeded in:
“[This] action represents the largest U.S.-led financial and technical disruption of a botnet infrastructure leveraged by cybercriminals to commit ransomware, financial fraud, and other cyber-enabled criminal activity.”
Needless to say, this is a huge win for our industry. We share the same sentiment as other cybersecurity practitioners, researchers, malware analysts and threat hunters in expressing a massive congratulations to law enforcement. This is a day of genuine celebration.
The public release statement from the Justice Department states that the collaborative effort between the United States, France, Germany, the Netherlands, the United Kingdom, Romania and Latvia made this operation possible.
They state, “the FBI was able to redirect Qakbot botnet traffic to and through servers controlled by the FBI, which in turn instructed infected computers [...] to download a file [...] that would uninstall the Qakbot malware.” 🔥
Additionally, the Department of Justice offers a number of documents and resources related to the Qakbot disruption, which This includes tactical information for victims, and pertinent applications and warrants.
Typically, Qakbot automates its delivery method in order to cast a wide net and infect as many potential victims as possible. It often lurks in the environment just to maintain persistence, so another threat actor can then obtain the access and consequently deploy ransomware, mine cryptocurrency, disrupt or deface software or any other post-exploitation effects.
Because Qakbot frequently remains dormant after its initial compromise, its persistence mechanisms are frequently overlooked—but it has the capability to collect keystrokes, harvest credentials, and move laterally throughout the network to further expand its access.
Fortunately, here at �Ӱɴ�ý, we’ve been laser-focused on persistence tradecraft since we started.
�Ӱɴ�ý has sent over 10,000 incident reports pertaining to Qakbot malware. We’ve seen firsthand an egregious amount of Qakbot infections, running rampant across the MSP/SMB space, so much so that and we worked to address it.
The botnet malware continued to affect our partners until the start of this year, when we worked to develop our own Qakbot "vaccine&��ܴdz�;.��
In late November of 2022, we started to look for creative ways to limit the effects of Qakbot. We would dig into the malware samples, do some reverse engineering and analysis, and consider different techniques that might prevent infection.
Since threat actors and cybercriminals need to remain stealthy, malware authors frequently implement techniques like defense evasion - tricks to avoid being flagged by automated tools like AV, EDR or others - and, namely, sandbox detection.
Say a security analyst or researcher would execute malware in a sandbox, or an environment purpose-built to monitor behavior and analyze what the malicious payload might do. The malware, wanting to remain undetected, will determine that it is running inside of a sandbox, and just terminate its execution so the program looks benign and innocent. This way, the sandbox might report this software is perfectly safe.
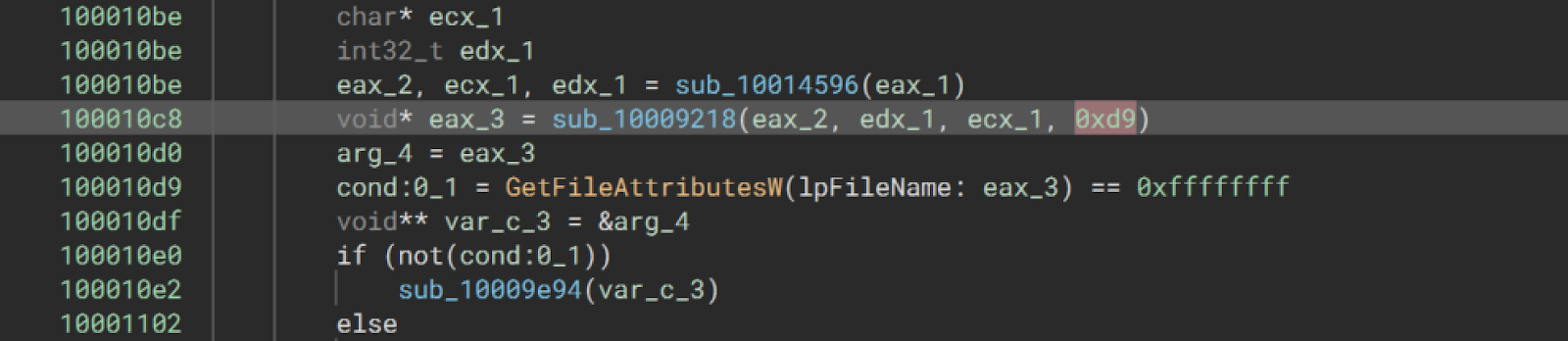
Here’s the kicker… Qakbot would check if it is in a sandbox. If the Qakbot malware found a unique artifact specific to the Windows Defender sandbox, it would just stop execution.
All credit to one of our finest reverse engineers, —Matthew uncovered that in the very early stages of execution, Qakbot would look for the presence of a C:\INTERNAL\__EMPTY file.
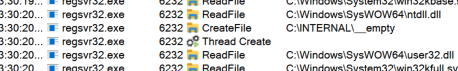
With that, we had a game plan: we could push out the C:\INTERNAL\__EMPTY file to our partner’s devices, and inoculate any new potential Qakbot infections!
We did a significant number of tests to validate that this was effective across multiple different Qakbot samples, and from everything we observed, the sandbox check was always present. We deployed this vaccine to all partner endpoints and monitored for file events.
Come the end of December 2022, we dropped the number of new Qakbot infection reports down to practically zero.
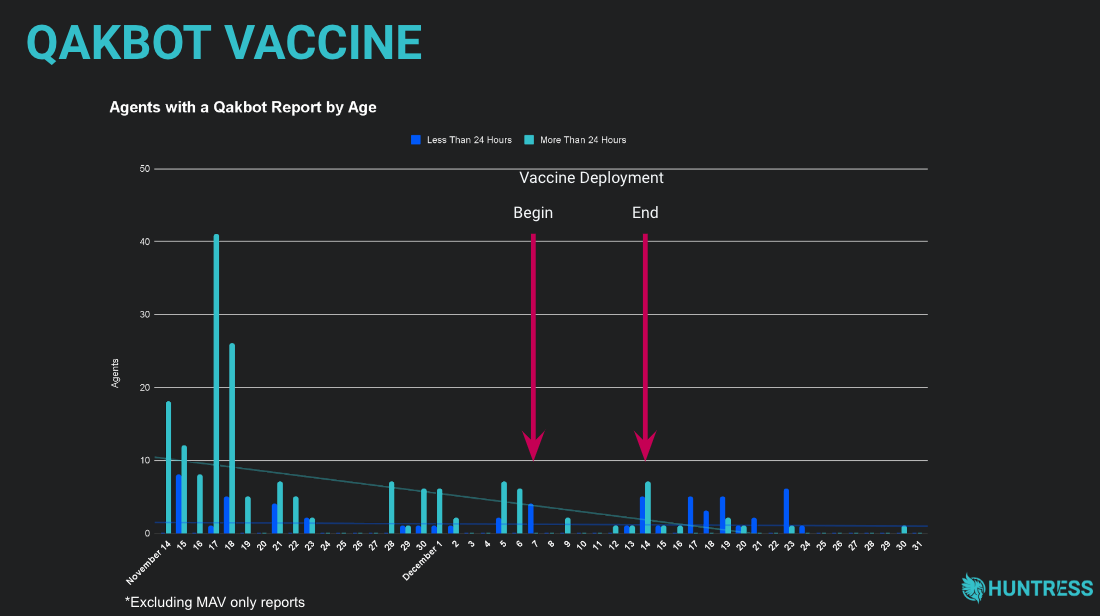
It worked! There was clear evidence that we made an impact and this simple but effective “vaccine” was really making a difference for the security of our partners.
The vaccine was rolled out to all our customers during a two-week period. Figure 3 above illustrates the number of Qakbot reports that were sent prior to, during, and after the vaccine rollout. The teal-colored bars indicate reports for machines that had the agent installed for more than 24 hours at the time the report was generated, and the dark blue bars indicate reports for machines that had newly installed the agent. You can see a clear drop in Qakbot reports as the vaccine deployment is initiated. There are a few spikes as infected machines start to come back online, or agents are newly installed on machines. Eventually, however, Qakbot reports became somewhat non-existent.
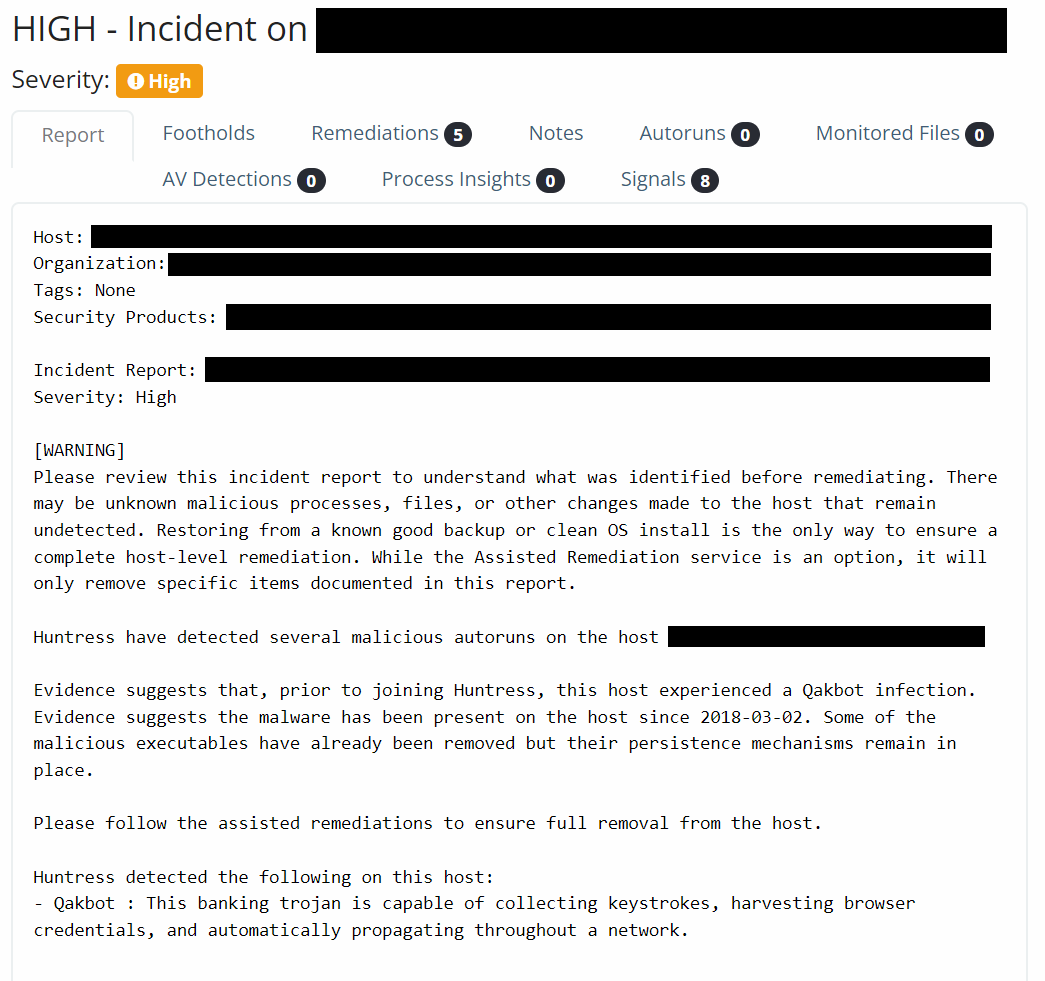
We still receive and report on leftover Qakbot infections that existed prior to �Ӱɴ�ý installation. If anything, these incidents add to the fact that Qakbot has been notoriously hard to uncover—sometimes dwelling in environments for years:
Our vaccine idea became an interesting discussion point for us internally… because we couldn’t exactly scream and shout about it publicly. We couldn’t celebrate on social media or tell the story in a blog post because then the threat actors could catch on and change up their tactics.
Think like a hacker for a moment: This is an easy change, right? Just don’t have the malware check for that sandbox artifact, and the fragile defensive mechanism is useless. We were cognizant of that and chose to not widely share the information.
However, already explicitly mention this C:\INTERNAL\__EMPTY file publicly. This isn’t a secret.
Obviously, telling this story now, you may think this explanation is counterintuitive. Aren’t we now burning the capability, showing our hand to the threat actors and just openly letting them adapt?
Well, we don’t think so. 😎
As other security vendors have already shared this detail and we’ve even on this vaccine file, we haven’t seen any change in Qakbot malware. Now, especially following the FBI takedown, we’re hopeful for the same.
More importantly, though, �Ӱɴ�ý wants to further the dialogue and ingenuity on how our industry can defend forward. We need more security practitioners and vendors looking for ways we can thwart our adversaries and bring the fight to cybercrime.
Following this FBI announcement, it’s not to say that the Qakbot botnet and malware strain has just been wiped from our world and they are gone for good—certainly, they may rebuild infrastructure and continue operations. The proactive FBI disruption may make a dent and hinder their work, but we know our industry is a cat-and-mouse game.
Perhaps in time, Qakbot will be back in action, but we remain cautiously optimistic.
With that said, our past work pales in comparison to the incredible initiative and result of the FBI and partners’ successful takedown. They shared a great message that it is the work that we do together that really combats today's threats.
This is another great foundation for our industry's need to defend forward and bring the fight to cybercrime on a global scale.
• • •
For analysts and researchers interested, the FBI code to remove the Qakbot malware and untether a host from the botnet is .
Special thanks to Matthew Brennan, Sharon Martin, Rob Noeth, Myles Keough, Kris Litman, and John Goedert for their contributions to our original Qakbot vaccine creation and rollout.
Get insider access to �Ӱɴ�ý tradecraft, killer events, and the freshest blog updates.
