







Cybersecurity professionals tend to focus more on the defensive side of security. That’s the nature of the job after all—when adversaries attack, we defend.��
But defense is only half of the equation.
Hackers are always evolving their tradecraft. They’re finding new ways to break into networks and systems, and they’re getting very good at defense evasion. With all the new tactics, techniques and procedures attackers are using, the traditional approach of defense-only cybersecurity isn’t enough.
Many businesses are realizing the need to develop both offensive and defensive strategies. But what’s best to focus on, playing offense or playing defense?
Defensive cybersecurity is all about blocking. This could come in the form of both tools and actions. You have your defensive tools that are designed to prevent or mitigate the effects of a cyberattack—such as antivirus software, firewalls, etc. And then you have your defensive actions, which include things like patching software and fixing system vulnerabilities.��
Offensive cybersecurity, on the other hand, is all about tackling and outmaneuvering. The focus here is on seeking out the hackers, and in some cases, attempting to disable or “hack back” to disrupt their operations. Offensive cybersecurity can also help identify vulnerabilities or weaknesses in your defense. It’s a slightly more proactive approach to security and can include practices like penetration testing and threat hunting.��
No matter which side of the field you’re on, the goal of any cybersecurity strategy should always be preventing the hackers (a.k.a. the opponent) from winning. But that brings us back to our original question: should we be playing offense or defense in cybersecurity?
The answer is both.��
The best teams know how to block and tackle. In cybersecurity, building the best possible defense means folding in some offensive strategies to gain intel on attackers and how they’re trying to penetrate your systems.
As I mentioned, almost every business or IT team has implemented the basics—that’s typically your AV, firewall, two-factor authentication, etc. But vulnerabilities exist at multiple touchpoints today and the basics just can’t keep up anymore.��
There’s no single layer of security that will keep you protected. To solve for this, we’ve started adding more layers and talking about defense in depth. With a multi-layered approach like defense in depth, the idea is to make initial access or compromise harder for the hacker. When you group a series of defenses together—like intrusion prevention, data encryption, supply chain management, user privilege policies and patch management—you effectively close the holes that one single solution can’t address.��
But of course, a fish will get through a net if it’s small enough. A forward will get past a defender if they’re fast enough. A hacker will get bypass defensive security layers if they’re skilled enough.��
One of the more problematic (and costly) gaps most businesses have is they lack the ability to identify attackers once they are already inside the network. So how are you expected to defend against something you don’t even know is there?
The key is faster threat detection, which starts by unleashing more offensive techniques to uncover the hackers who are hiding in your environment.��
The hardest part is that this first requires a mindset shift—from doing all you can to prevent a breach, to assuming compromise and hunting for clues or breadcrumbs. That’s the main idea behind zero trust security.��
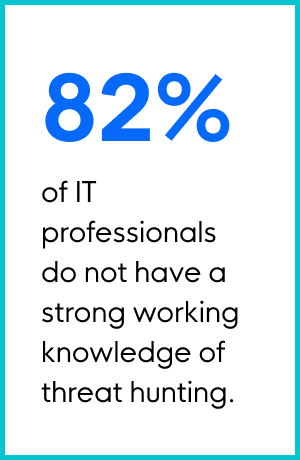
One of the better ways to get on offense is to go threat hunting. Threat hunting is an offensive technique of searching for cyber threats that are lurking in the shadows. But according to a 2020 survey we took of 350+ IT professionals, 82% claimed they do not have a strong working knowledge of threat hunting.
Essentially, threat hunting allows you to turn the tables on attackers and take a more proactive approach to cybersecurity. Whether through an internal team or partnership, having defenders proactively looking for indicators of pending or active threats can make all the difference in stopping cyberattacks in their tracks.��
Instead of waiting to be notified of a breach, this approach heavily relies on threat intelligence and understanding hacker tradecraft.
And the best threat hunting doesn’t rely on automation or artificial intelligence to do this—it uses human analysts who can think like the enemy and know how to identify warning signs.
Of course, there’s a level of skill and knowledge required to be a threat hunter—which brings me to the next best offensive technique: education.��
Recommended Reading: Why Cybersecurity Education is the Key To Outsmarting Hackers
Continuous learning and cyber education can help fine-tune your skills and stay one step ahead of attackers. For example, capture the flag challenges like or are great exercises to boost your own knowledge and put your skills to the test. There’s also no shortage of cybersecurity-focused events and conferences you can attend to exchange experiences with your peers and hear from experts on how they go about handling and mitigating the latest threats.
If you’re ready to level up your skills, you should re-watch all of our sessions from hack_it 2021.2! You'll learn from industry experts as they solve cyber crimes, peer into the corners of the dark web and even cook up some macro-enabled malware. Our sessions were packed with useful tips and tricks—if you missed the live event, you can catch all the recordings here.
Get insider access to �Ӱɴ�ý tradecraft, killer events, and the freshest blog updates.
