







Sometimes change happens so gradually it’s easy to miss. That’s often the case in cybersecurity.
We see statements like “the security landscape is evolving” or “hackers are getting smarter” that just get brushed off as the latest marketing lingo, but they actually hold some serious weight if you stop to think about it.��
At �Ӱɴ�ý, our days are dedicated to studying and learning from hacker tradecraft. We want to understand exactly how attackers operate so we can pick up on their tricks and tactics and know how to defend against them. We know that in order to prepare for the future, we can’t dismiss the past. Read on for a brief history of how hackers are evolving their tradecraft and how it can help us better prepare for tomorrow’s threats.
Looking back, the world’s approach to cybersecurity has been mostly reactionary. We settled into “new attack, new security product” mode, where the attacks and threats themselves were driving the creation of protective products.
In the 1980s, for example, virus attacks on stand-alone PCs affected all businesses—which drove the development of commercial antivirus software to protect against them. As we moved along to the mid 1990s, the internet opened the gates for the broad and rapid spread of malware—which then introduced us to the firewall.��
But as time went on, cyberattacks could not be effectively stopped by firewalls or antivirus products alone. Hackers learned to leverage vulnerabilities—masking their attacks in anything from resumes to picture files, behind which awaited sophisticated code that was ready to launch. All they needed was a user to open an email attachment or plug in a USB and the attack was silently unleashed.��
In response, the IT industry boomed in the early 2000s—bringing with it fresh products and services to meet the needs of a hungry market. We saw new technologies emerge like signature-based detection, automation and artificial intelligence. But all the while, hackers were watching and learning how to beat these tools.
What began as inquisitive teenagers hacking for the sheer fun and challenge of it all has now turned into a more organized and formidable force. Hacker motives changed from recognition and notoriety to being in it for the money—turning cybercrime into a multi-billion dollar industry.
Today’s hackers have moved beyond the Hollywood stereotype of the lone hacker in a basement. Instead, they’re operating in highly organized groups (very similar to the professional environments we’re all familiar with). And not only has this dynamic introduced a more economically-focused adversary, it has also provided a wider distribution of hacker skills and know-how.
There’s more knowledge and resources at a hacker’s fingertips than ever before. Look no further than the dark web. It’s got malicious gadgets and gizmos a-plenty, even keyloggers and wipers galore. You want a hacker for hire? There are many.��
The point is: modern hackers know there is money to be made in cybercrime and they’re using the dark web to source tools or skills that they might not have—and this has completely changed the way bad actors go about their attacks.
Most attackers will go for the low-hanging fruit and use the path of least resistance. Phishing is a popular choice for that reason—you can use malicious links and fake documents to lure users into clicking or opening something.��
And while phishing is an effective way to gain initial access, if the user shuts down their computer, the attacker has just lost their access. Can you imagine if any time that happened, the hacker would just re-phish the user? That would be the world’s most efficient hacker!
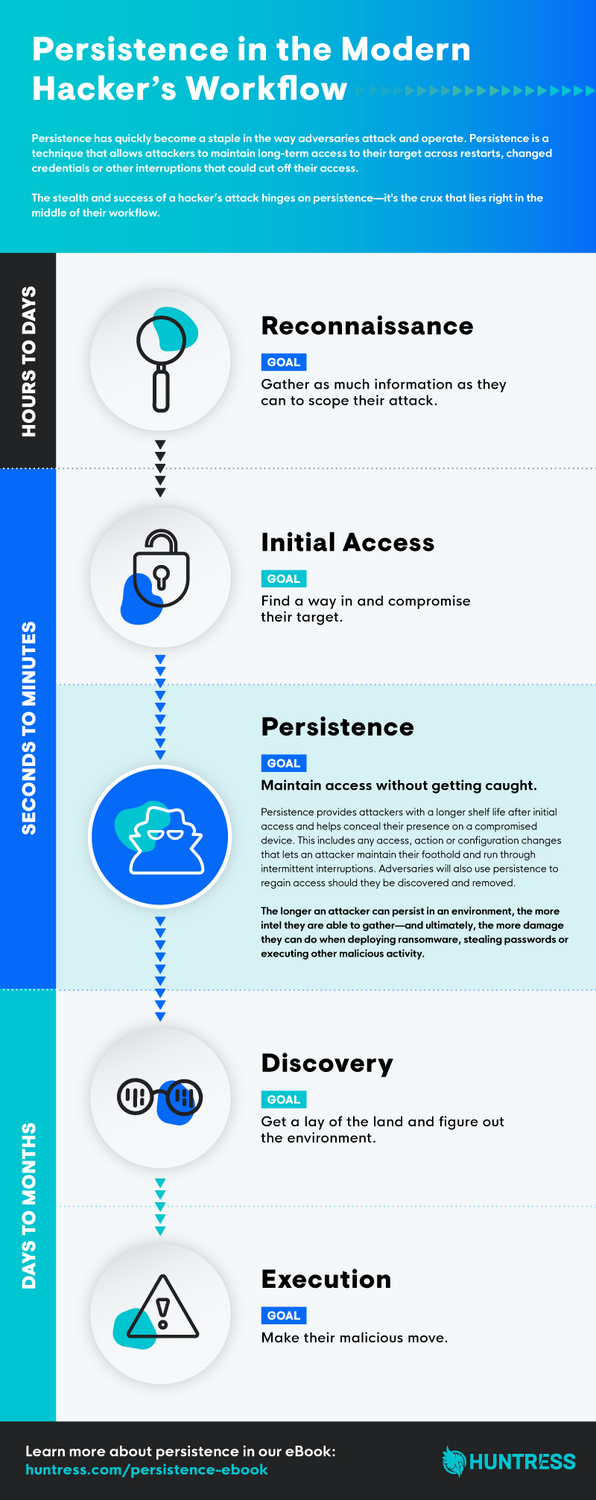
Getting in is no longer the hard part, it’s staying in. That’s where persistence comes in handy for hackers.
Attackers are turning away from methods that are easy to detect and shut down. Instead, more and more bad actors are opting for a “low-and-slow” approach, establishing persistence to lay low and maintain long-term access to their targets.
Although slower, this persistent strategy enables more covert operations. Here’s a look at how hackers are using persistence in their attacks.
��
At the end of the day, all cyberattacks are not created equal—nor are all cybercriminals. Some are more persistent than others, so it’s becoming increasingly important to understand our adversaries and better equip ourselves for the fight.
Want to learn more?
Get insider access to �Ӱɴ�ý tradecraft, killer events, and the freshest blog updates.
