






Cybercriminals are constantly refining their tactics and attack methodologies. With growing threats like session hijacking and credential theft, these aren‚Äôt just buzzwords‚Äîthey‚Äôre real threats that all organizations (regardless of size or industry) can‚Äôt afford to ignore.¬Ý
According to IBM's 2024 X-Force Threat Intelligence Index, the abuse of valid credentials was the top initial access vector in 2023, accounting for 30% of incidents, while session hijacking vulnerabilities were found in 15% of all security misconfigurations identified globally.¬Ý
Session hijacking and credential theft are a big deal. As hackers evolve their methods, organizations must strengthen their defenses and protect their identity attack surface from hackers looking to wreak havoc.¬Ý
At –”∞…¥´√Ω, we‚Äôve seen how session hijacking and credential theft are critical vectors that hackers exploit to gain unauthorized access to your business-critical assets. That‚Äôs why the –”∞…¥´√Ω Managed Identity Threat Detection and Response (ITDR)¬Ýteam has introduced Unwanted Access, a new capability focused on wrecking hackers by shutting down the primary ways they take over accounts: session hijacking and credential theft.
We’ve taken our partners’ input to heart in developing Unwanted Access. We start by analyzing Microsoft 365 events, organizing them into sessions, and then incorporating partner and customer feedback about expected and unauthorized VPNs and locations via Unwanted Access configuration rules. This capability zeroes in on tradecraft in the earlier phases of the attack lifecycle and provides identity isolation to mitigate compromises before they escalate.
There are a few new features and functionalities you can expect to see with Unwanted Access.¬Ý
To give our partners and customers greater configuration control, Unwanted Access rules empower you to tune your environment and help our Security Operations Center (SOC) better baseline your identity behaviors. How does this work? At any time, you can create ‚ÄúExpected‚Äù and ‚ÄúUnauthorized‚Äù rules for locations and VPNs.¬Ý
For example, if your business is located in the United States and you know that you never anticipate login activity from, say, Egypt, you can create an expected rule for the United States and an unauthorized rule for Egypt.
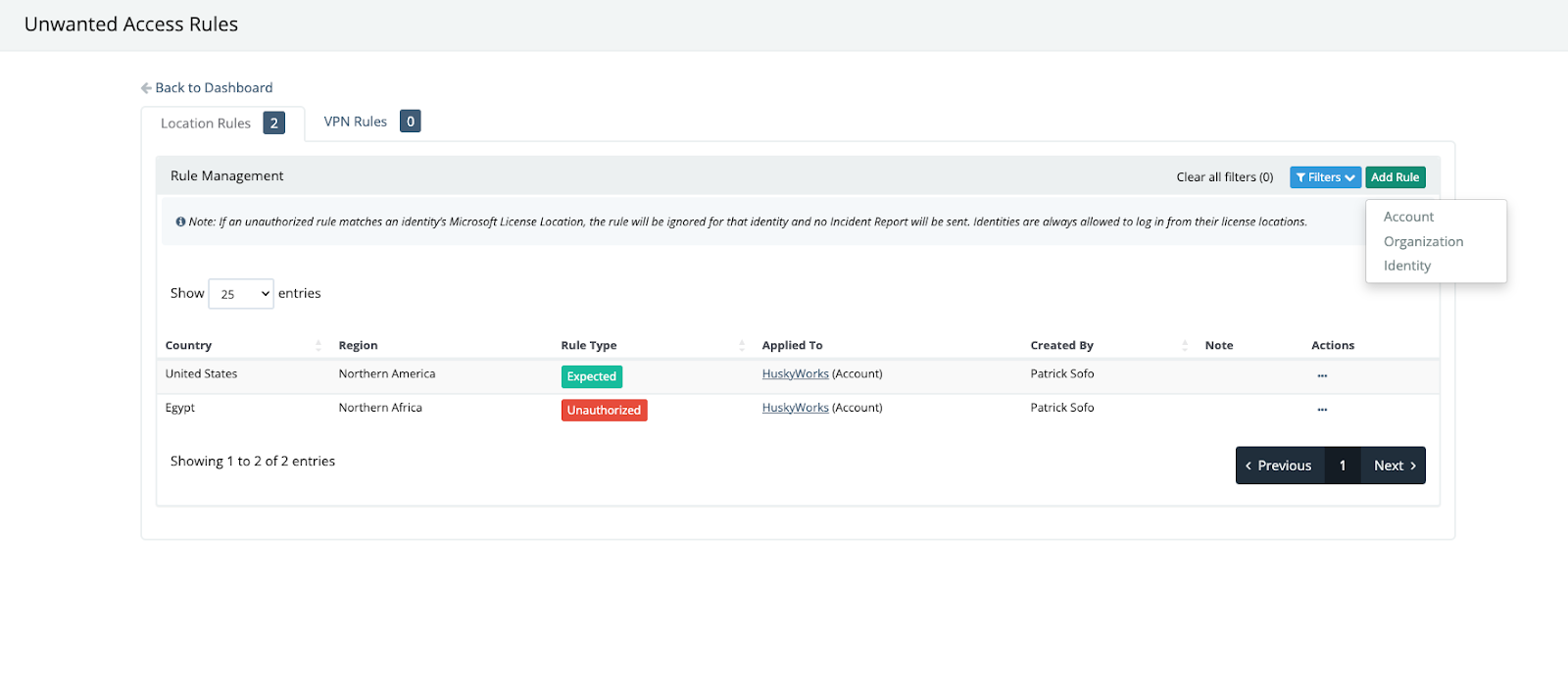
Once these rules are created, all login activity from the United States would be deemed ‚Äúknown,‚Äù and any login activity from Egypt would be considered malicious. Our SOC would send an incident report alerting on the activity.¬Ý
Setting a location or VPN as ‚ÄúExpected‚Äù doesn't prevent the –”∞…¥´√Ω SOC from seeing login data related to that location or investigating it to see if it seems out of the ordinary. In fact, we evaluate ALL login events for malicious activity, even if expected configuration rules are set for a particular location or VPN. These rules provide contextual information to the SOC and are important in reducing false alerts in your environment.
Unwanted Access rules also apply to VPNs. Confident that you won’t be logging in from YouShallNotPass VPN? Simply add it to the “Unauthorized” list.
What‚Äôs more, you‚Äôre able to create Unwanted Access rules for locations or VPNs at the account, organization, or identity level.¬Ý
We‚Äôve also introduced escalations as part of Unwanted Access. Escalations help our SOC gather more information when investigating Unwanted Access login activity. These are not active incidents. Rather, they‚Äôre flags for situations where we need more information to decide on next steps. If we spot a login from an unknown country or VPN, we‚Äôll send an escalation to help determine if it‚Äôs legitimate or unauthorized.¬Ý
For example, a partner has created expected location rules for the United States and Ireland and an unauthorized location rule for Romania. But, we see unknown login activity from France. Because we need more information from the partner to determine if this login activity is malicious, we send an escalation prompting the partner to create an Expected or Unauthorized rule for this location.¬Ý
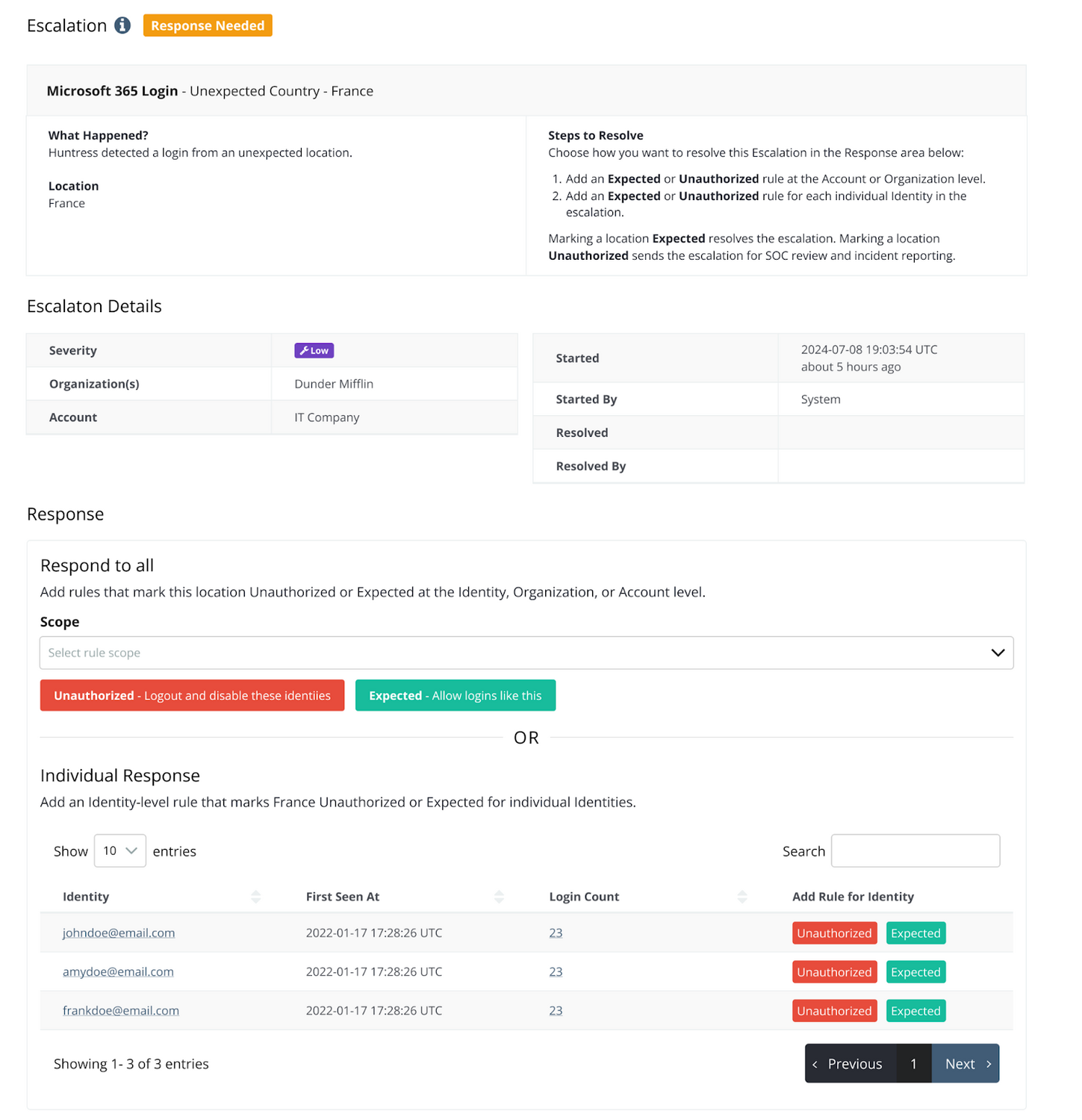
Escalations are sent via email and PSA, and are available in the –”∞…¥´√Ω portal.
As threats continue to evolve, our new Unwanted Access functionality empowers you to stay one step ahead of cyber threats by proactively addressing session hijacking and credential theft. Our advanced detection and response capabilities give you the ability to customize and tune your security environments to ensure that only authorized users have access to business-critical assets. Plus, Unwanted Access configuration rules and escalations provide clear visibility and control over your Microsoft 365 identity landscape, further empowering you to take charge of your security like never before.
Ready to try Managed ITDR's new Unwanted Access? Sign up for a free trial today.
Get insider access to –”∞…¥´√Ω tradecraft, killer events, and the freshest blog updates.
